

![]()
UXP Technology is not an encryption tool. UXP Technology is not a security replacement.
![]()
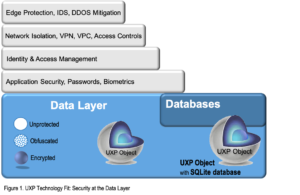
UXP Technology is an enhancement to the existing security layers in any organization. UXP Technology enhances the existing security model by embedding intelligence and protection policies for access control into the data. From data’s creation through its expiration or destruction, UXP Technology focuses on protecting the entire data life-cycle.
![]()
At the beginning of the data life-cycle, UXP Technology transforms your data into a UXP Object, an intelligent, proactive entity.
This transformation NEVER modifies the original data.
As a UXP Object, this entity is able to enforce embedded protection policies for access control wherever the Object resides. The protection policies, defined by the data owner, are suited for the data’s security requirements.
During the data’s active life-cycle, the embedded UXP Intelligence and protection policies empower the UXP Object to enforce the policies without deviation while the data is:
The data owner stays in control of their data at all times.
This control remains in place during the UXP Object’s entire life-cycle. The Object life-cycle is complete when one of the following events occur:
![]()
UXP Protection Scheme is a unique protocol. UXP Technology uses proprietary algorithms that blend in obfuscation and cloaking along with standard AES 256-GCM encryption algorithms.
The overall UXP Protection Scheme is embedded in the UXP Object.
The following components participate in the protection scheme generation:
*Distinct Differentiator in the UXP Protection Scheme: The protection protocol generates and embeds a key management system in the UXP Object. This system allows the UXP Object to manage the keys internally. Randomly generated when the data is protected, the embedded encryption keys are cloaked, inaccessible and never shared.
![]()
UXP Technology’s Intelligence solves the data security issue by embedding access controls, risk mitigations, and defensive mechanisms within the UXP Object. UXP Technology empowers the data through the UXP Object to be intelligent and proactive.
The actions listed below are samples of UXP Intelligence capabilities:
![]()
UXP Technology in Healthcare Brochure
![]()